
Scattered Spider continues to dominate the headlines, with the most recent information linking the hackers to assaults on U.S. insurance coverage large Aflac, Philadelphia Insurance coverage Firms, and Erie Insurance coverage, disclosed by way of SEC Type 8-Ok filings which point out the theft of delicate buyer knowledge and operational disruption.
This comes on the identical time that Google Risk Intelligence Group shared that it “is now conscious of a number of intrusions within the U.S. which bear the hallmarks of Scattered Spider exercise”, particularly impacting the insurance coverage trade.
However what precisely does this imply? To reply this, let’s shortly recap how we acquired right here and what a Scattered Spider assault seems like.
How did we get right here?
The legal collective tracked by analysts as Scattered Spider has been energetic since 2022 and have been linked to a variety of high-profile breaches, for instance the assaults on Caesars and MGM Resorts in 2023, and Transport for London in 2024.
-
Caesars: hackers impersonated an IT consumer and satisfied an outsourced assist desk to reset credentials, after which the attacker stole the client loyalty program database and secured a $15m ransom cost.
-
MGM Resorts: hackers used LinkedIn info to impersonate an worker and reset the worker’s credentials, leading to a 6TB knowledge theft. After MGM refused to pay, the assault ultimately resulted in a 36-hour outage, a $100m hit, and a class-action lawsuit settled for $45m.
-
Transport for London: resulted in 5,000 customers’ financial institution particulars uncovered, 30,000 employees required to attend in-person appointments to confirm their identities and reset passwords, and vital disruption to on-line providers lasting for months.
The calling card in these assaults was the abuse of assist desk processes to reset passwords and/or MFA elements used to entry an account.
The attacker merely calls up the assistance desk with sufficient info to impersonate an worker, asks them to ship an MFA enrollment hyperlink for his or her new cellular system, and might then make the most of self-service password reset performance to take management of the account. Scarily easy.
Scattered Spider has dominated the information in latest weeks following high-profile breaches impacting UK retailers. However with a protracted historical past of high-profile ransomware assaults, this is only one instance of their identity-based strategy.
Be part of Push Safety as they transcend the breaches and discover ways to defend your group in opposition to Scattered Spider’s rising arsenal of TTPs.
Scattered Spider’s resurgence in 2025
This system was reprised in a sequence of high-profile assaults in 2025, with main breaches of UK retailers Marks and Spencer and Co-op dominating the headlines.
Each resulted within the lack of delicate knowledge and extended disruption to in-store and digital providers, with M&S feeling the ache of £300m in misplaced income and a share worth hit approaching £1b, and a multimillion-pound class motion lawsuit and doable ICO fines looming.
A sequence of assaults in opposition to retailers worldwide quickly adopted, at an unprecedented charge. Dior, The North Face, Cartier, Victoria’s Secret, Adidas, Coca-Cola, and United Pure Meals have been among the many retailers to endure a breach between Could-June 2025.
Not like the mass Snowflake breaches in 2024 (which focused a single platform utilized by many organizations), these assaults are notable in that they’re seemingly unrelated — they merely symbolize a concerted effort by attackers to focus on the retail sector.
Much less particulars have been supplied about these assaults in comparison with the M&S and Co-op breaches, however various them particularly level to using identity-based methods versus extra conventional software program exploits — one other hallmark of Scattered Spider.
This leads us to our first key takeaway…
Takeaway #1: Identification-based TTPs are the brand new regular
Scattered Spider’s assaults are the most recent in a rising variety of identity-based breaches. After we look again at Scattered Spider’s TTP evolution, we will see that they’ve persistently exploited identity-based weaknesses as a way to achieve entry to sufferer environments.
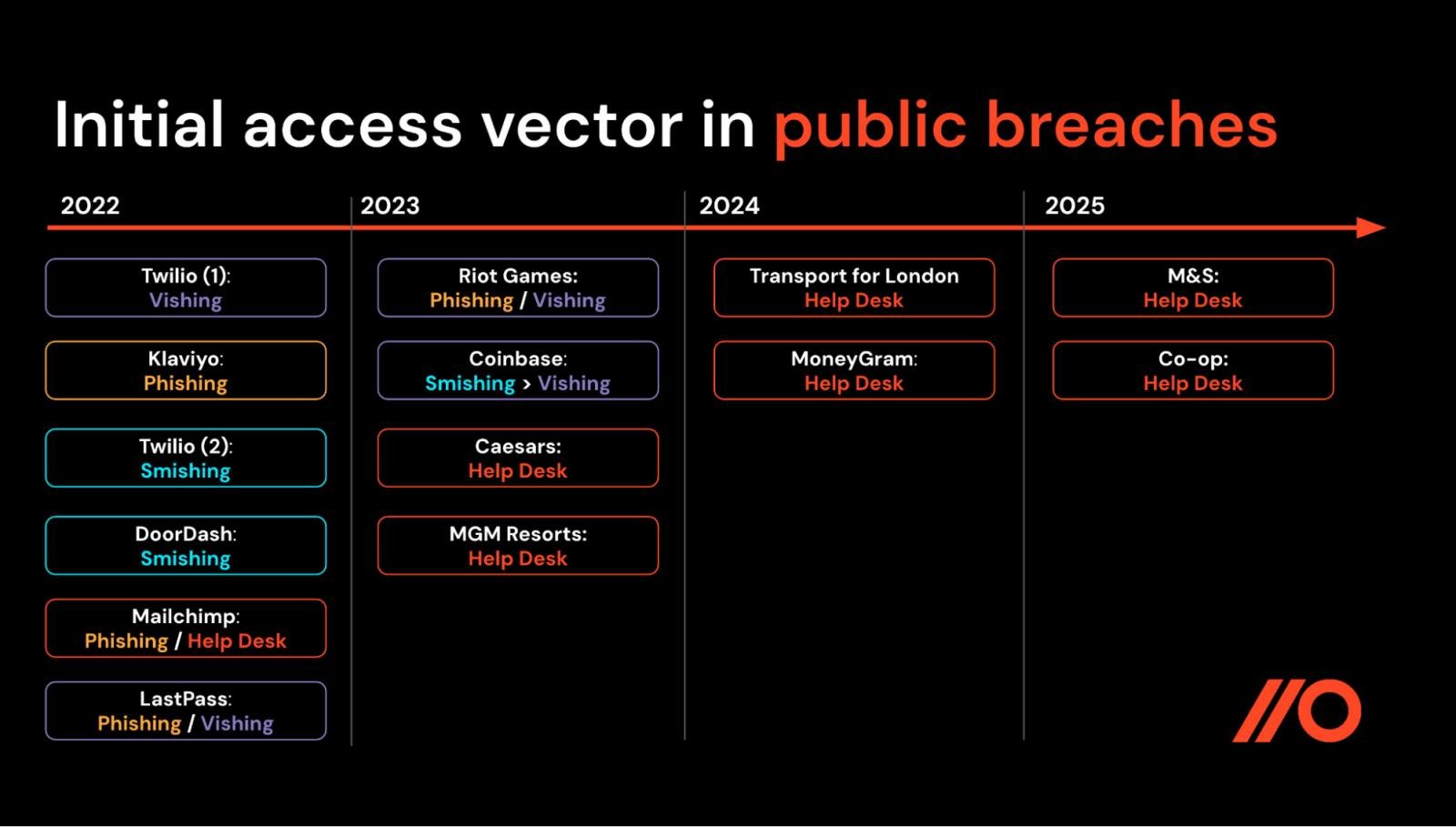
Supply: Push Safety.
Taking a step again, it’s value interested by how assist desk scams match into the broader toolkit of techniques, methods and procedures (TTPs) utilized by menace actors like Scattered Spider.
Scattered Spider has closely relied on identity-based TTPs since they first emerged in 2022, following a repeatable path of bypassing MFA, reaching account takeover on privileged accounts, stealing knowledge from cloud providers, and deploying ransomware (principally in VMware environments). TTPs utilized by Scattered Spider embrace:
-
Credential phishing by way of electronic mail and SMS (smishing) to reap passwords en masse
-
Utilizing SIM swapping (the place you get the provider to switch a quantity to your attacker-controlled SIM card) to bypass SMS-based MFA
-
Utilizing MFA fatigue (aka. push bombing) to bypass app-based push authentication
-
Utilizing vishing (i.e. instantly calling a sufferer to social engineer their MFA code, versus a assist desk assault)
-
Social engineering area registrars to take management of the goal group’s DNS, hijacking their MX data and inbound mail, and utilizing this to take over the corporate’s enterprise app environments
-
And latterly, utilizing MFA-bypass AiTM phishing kits like Evilginx to steal dwell consumer periods
So, assist desk scams are an essential a part of their toolkit, nevertheless it’s not the entire image. Strategies like AiTM phishing particularly have spiked in recognition this yr as a dependable and scalable means of bypassing MFA and reaching account takeover.
It’s essential not to consider these methods as only a Scattered Spider trait both. In spite of everything, Scattered Spider isn’t a self-identified group — it’s a reputation given by analysts to patterns of exercise. Given the sequence of arrests in 2024, it’s unlikely that the present incarnation of Scattered Spider is identical people behind the assaults in 2022-2024.
And these identity-based assault patterns are shared throughout numerous self-named legal teams like, Lapsus$, Yanluowang, Karakurt, and ShinyHunters. Even Russian state-sponsored actors are more and more utilizing the sorts of methods popularised by legal teams.
Merely, identity-based methods are the brand new regular for attackers in 2025.
Takeaway #2: Assist desk scams aren’t new, however they’re right here to remain
As we established earlier, assist desk scams are nothing new (we noticed them within the Caesars, MGM Resorts, and Transport for London breaches to call a number of). However they’re more likely to develop into more and more prevalent as Scattered Spider continues to display simply how efficient assist desk scams are.
One of many causes they’re so efficient is that almost all assist desks have the identical course of for each account — it doesn’t matter who you’re impersonating or which account you’re making an attempt to reset.
So, attackers are particularly concentrating on accounts more likely to have high tier admin privileges — which means as soon as they get in, progressing the assault is trivial and far of the everyday privilege escalation and lateral motion is faraway from the assault path.
Assist desks are a goal for a purpose. They’re “useful” by nature. That is normally mirrored in how they’re operated and efficiency measured — delays gained’t show you how to to hit these SLAs!
Finally, a course of solely works if staff are prepared to stick to it — and might’t be socially engineered to interrupt it. Assist desks which might be faraway from day-to-day operations (particularly when outsourced or offshored) are additionally inherently inclined to assaults the place staff are impersonated.
However, the assaults that organizations are experiencing in the intervening time ought to give safety stakeholders loads of ammunition as to why assist desk reforms are very important to securing the enterprise (and what can occur in the event you don’t make adjustments).
Takeaway #3: Scattered Spider are consciously evading established safety controls
So, there’s extra to Scattered Spider’s toolkit than simply assist desk scams. In actual fact, their strategy could be broadly categorized as consciously evading established controls on the endpoint and community layer by concentrating on identities.
From the purpose of account takeover, in addition they comply with repeatable patterns:
-
Harvesting and exfiltrating knowledge from cloud and SaaS providers, the place monitoring is usually much less constant than conventional on-premise environments, and exfiltration usually blends in with regular exercise. Many organizations merely don’t have the logs or visibility to detect malicious exercise within the cloud anyway, and Scattered Spider have additionally been seen tampering with cloud logs (e.g. filtering dangerous AWS CloudTrail logs, however not disabling it fully in order to not elevate suspicion).
-
Focusing on VMware environments for ransomware deployment. They do that by including their compromised consumer account to the VMware admins group in VCentre (if wanted — they’re going after accounts with high tier privileges by default). From right here, they will entry the VMware setting by way of the ESXi hypervisor layer, the place safety software program is nonexistent — thereby bypassing EDR and different typical endpoint and host primarily based controls you depend on to forestall ransomware execution.
The important thing theme? Getting round your established safety controls.
Trendy assaults not happen on the endpoint or community — they aim identities created and used by way of the net browser. Because of this assaults more and more happen within the browser (or moderately, on assets your staff entry by way of the browser).
Push Safety’s browser-based safety platform supplies complete id assault detection and response capabilities in opposition to methods like AiTM phishing, credential stuffing, password spraying and session hijacking utilizing stolen session tokens.
It’s also possible to use Push to search out and repair id vulnerabilities throughout each app that your staff use, like: ghost logins; SSO protection gaps; MFA gaps; weak, breached and reused passwords; dangerous OAuth integrations; and extra.
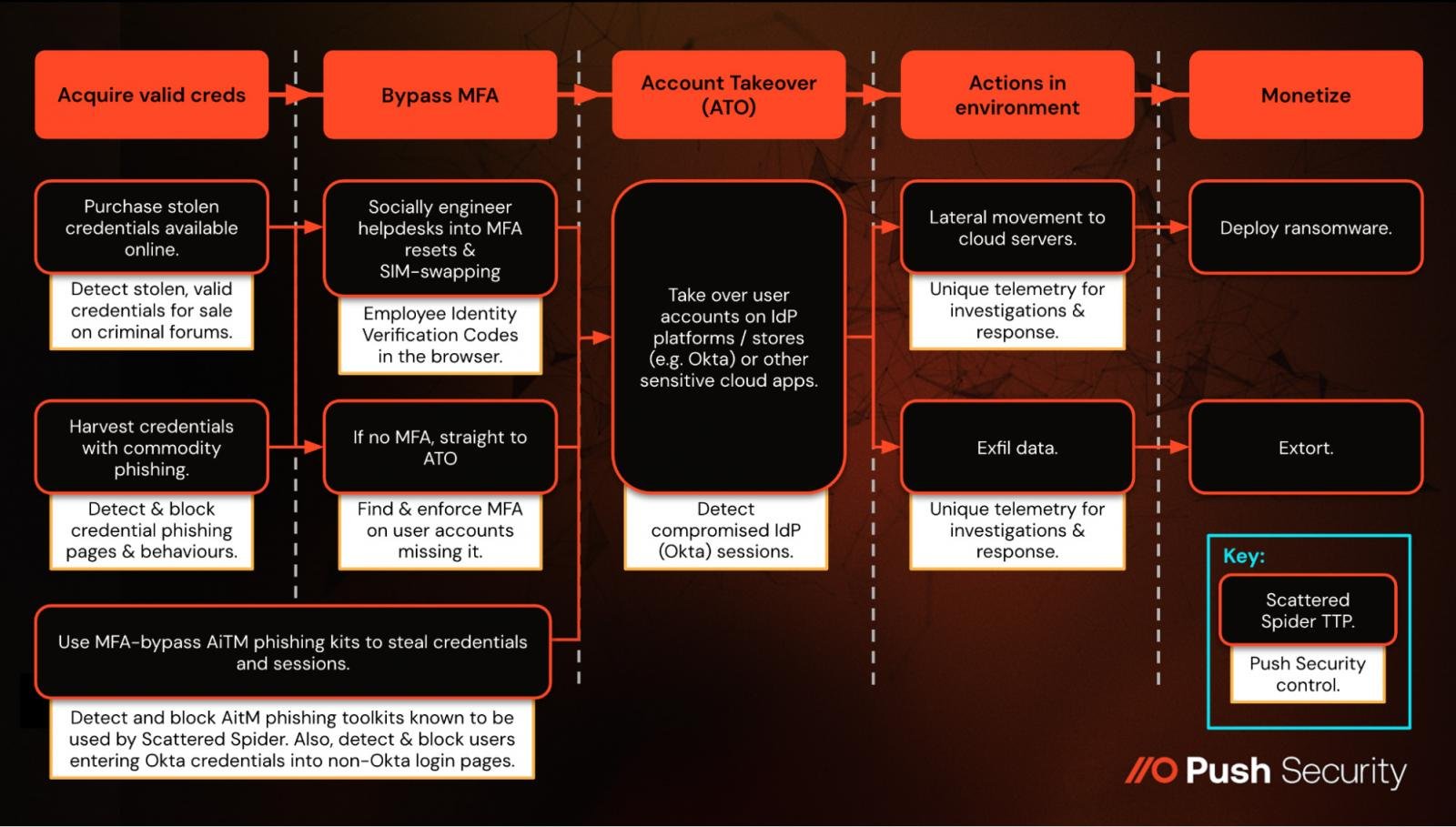
Supply: Push
To assist fight assist desk scams, Push lately launched Worker Identification Verification Codes — a easy, browser-based id test that offers your assist desk a dependable approach to affirm they’re speaking to somebody out of your group.
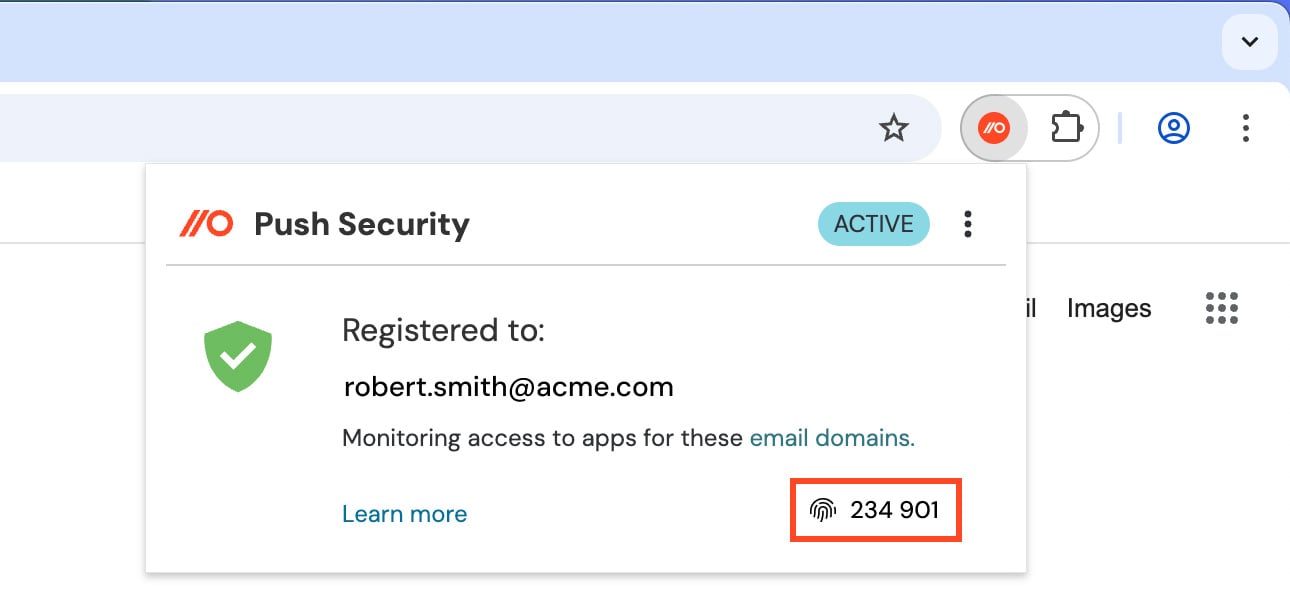
Push supplies a light-weight verification function in each consumer’s browser — no further apps or gadgets required.
It allows reputable assist desk callers to shortly confirm that they’re in possession of their main system (i.e. laptop computer) by relaying a rotating 6-digit verification code of their browser by way of the Push extension.
It is a nice approach to securely affirm caller id and sniff out fraudulent callers, and can be utilized as a part of a phishing-resistant assist desk course of.
Eric Rubin — a Senior Supervisor in GitLab’s Company Safety staff — has already rolled out Worker Identification Verification Codes throughout his workforce. Right here’s what he needed to say:

Get began as we speak!
You should use Worker Verification Codes as a free instrument by putting in the Push browser extension. Merely join a trial account and you may deploy the extension organization-wide to utilize this function.
Whilst you’re at it, you’ll be able to trial Push’s full options for as much as 10 customers without cost.
Or if you wish to be taught extra about how Push lets you detect and defeat widespread id assault methods, e-book a while with one in all our staff for a dwell demo.
Sponsored and written by Push Safety.


